Overview
Static Application Security Testing (SAST) is a white-box security testing methodology that analyzes source code, bytecode, or binary code to identify security vulnerabilities without executing the application. Codepure’s SAST solution provides deep code analysis capabilities that integrate seamlessly into your development workflow, enabling you to build secure software from the ground up.What is SAST?
Codepure’s SAST engine performs comprehensive security analysis of your application’s source code during the development phase. By examining code structure, data flows, and control flows, SAST identifies security vulnerabilities, quality issues, and compliance violations before they reach production.Core Capabilities
- Deep Code Analysis: Examines code paths, data flows, and control structures
- Language-Agnostic Scanning: Supports 30+ programming languages and frameworks
- Incremental Scanning: Analyzes only changed code for faster feedback
- Custom Rule Engine: Define organization-specific security policies
- AI-Powered Detection: Machine learning models identify complex vulnerability patterns
- Developer-Friendly Reporting: Clear, actionable remediation guidance
How SAST Works
Analysis Methodology
Codepure SAST employs multiple analysis techniques for comprehensive coverage:1. Lexical Analysis
- Tokenizes source code into meaningful components
- Identifies dangerous functions and deprecated methods
- Detects hardcoded secrets and credentials
2. Syntactic Analysis
- Builds Abstract Syntax Trees (AST) of your code
- Validates code structure and patterns
- Identifies anti-patterns and insecure constructs
3. Semantic Analysis
- Understands code behavior and intent
- Tracks variable states and transformations
- Analyzes type safety and memory management
4. Data Flow Analysis
- Traces data movement through the application
- Identifies tainted data sources
- Tracks data sanitization and validation
5. Control Flow Analysis
- Maps all possible execution paths
- Identifies unreachable code and dead ends
- Detects race conditions and timing issues
Vulnerability Detection Categories
Injection Flaws
- SQL Injection: Unsanitized database queries
- Command Injection: OS command execution vulnerabilities
- LDAP Injection: Directory service query manipulation
- XPath Injection: XML query vulnerabilities
- NoSQL Injection: Document database vulnerabilities
Authentication & Session Management
- Weak password policies
- Insecure session handling
- Missing authentication checks
- Privilege escalation paths
- Broken authentication flows
Cross-Site Scripting (XSS)
- Reflected XSS: Immediate execution vulnerabilities
- Stored XSS: Persistent script injection
- DOM-based XSS: Client-side script vulnerabilities
Security Misconfiguration
- Hardcoded credentials
- Insecure default settings
- Verbose error messages
- Unnecessary features enabled
- Missing security headers
Sensitive Data Exposure
- Unencrypted data transmission
- Weak cryptographic algorithms
- Improper key management
- Data leakage in logs
- Insufficient data masking
Access Control Issues
- Path Traversal: Directory traversal vulnerabilities
- Insecure Direct Object References: Unauthorized data access
- Missing Function Level Access Control: Unprotected APIs
- CORS Misconfiguration: Cross-origin resource sharing issues
Business Logic Flaws
- Race conditions
- Time-of-check to time-of-use (TOCTOU)
- Improper input validation
- Integer overflow/underflow
- Buffer overflows
Why SAST is Critical
Security Benefits
Shift-Left Security- Integrate security into the earliest stages of development
- Reduce the cost of vulnerability remediation by 100x
- Prevent vulnerabilities from reaching production
- Analyze 100% of your codebase
- Detect vulnerabilities in rarely executed code paths
- Identify issues in third-party integrations
- Automated scanning on every commit
- Real-time security feedback during development
- Progressive security improvement over time
Business Impact
Cost Reduction
- Early Detection: Fix vulnerabilities when they’re 100x cheaper to resolve
- Automated Testing: Reduce manual security review overhead
- Prevent Breaches: Avoid costly security incidents and data breaches
Accelerated Development
- Instant Feedback: Developers get security insights in real-time
- Automated Remediation: AI-powered fix suggestions
- Reduced Rework: Fewer security issues in later stages
Compliance Assurance
- Meet regulatory requirements (GDPR, HIPAA, PCI DSS)
- Satisfy security audit requirements
- Demonstrate due diligence in software security
Supported Technologies
Programming Languages
Web Technologies- JavaScript/TypeScript (Node.js, React, Angular, Vue)
- Python (Django, Flask, FastAPI)
- PHP (Laravel, Symfony, WordPress)
- Ruby (Rails, Sinatra)
- Java (Spring, Struts, JSF)
- C# (.NET Core, ASP.NET)
- Go
- Scala
- Kotlin
- C/C++
- Rust
- Swift
- Objective-C
- Android (Java/Kotlin)
- iOS (Swift/Objective-C)
- React Native
- Flutter/Dart
- Terraform
- CloudFormation
- Ansible
- Kubernetes YAML
Frameworks and Libraries
Codepure maintains an extensive database of framework-specific security rules:- Spring Security patterns
- Django security middleware
- Express.js security configurations
- React security best practices
- And 100+ more frameworks
Using Codepure SAST
Quick Start Guide
1. Initiate Scan
Configure and launch your SAST analysis:- Navigate to your project dashboard
- Select the repository or upload code
- Choose SAST from the scanner options
- Configure scan parameters:
- Select rule sets (OWASP, CWE, Custom)
- Set severity thresholds
- Choose incremental or full scan
- Click Start Scanning to begin analysis
2. Review Results
Access detailed vulnerability findings with contextual information: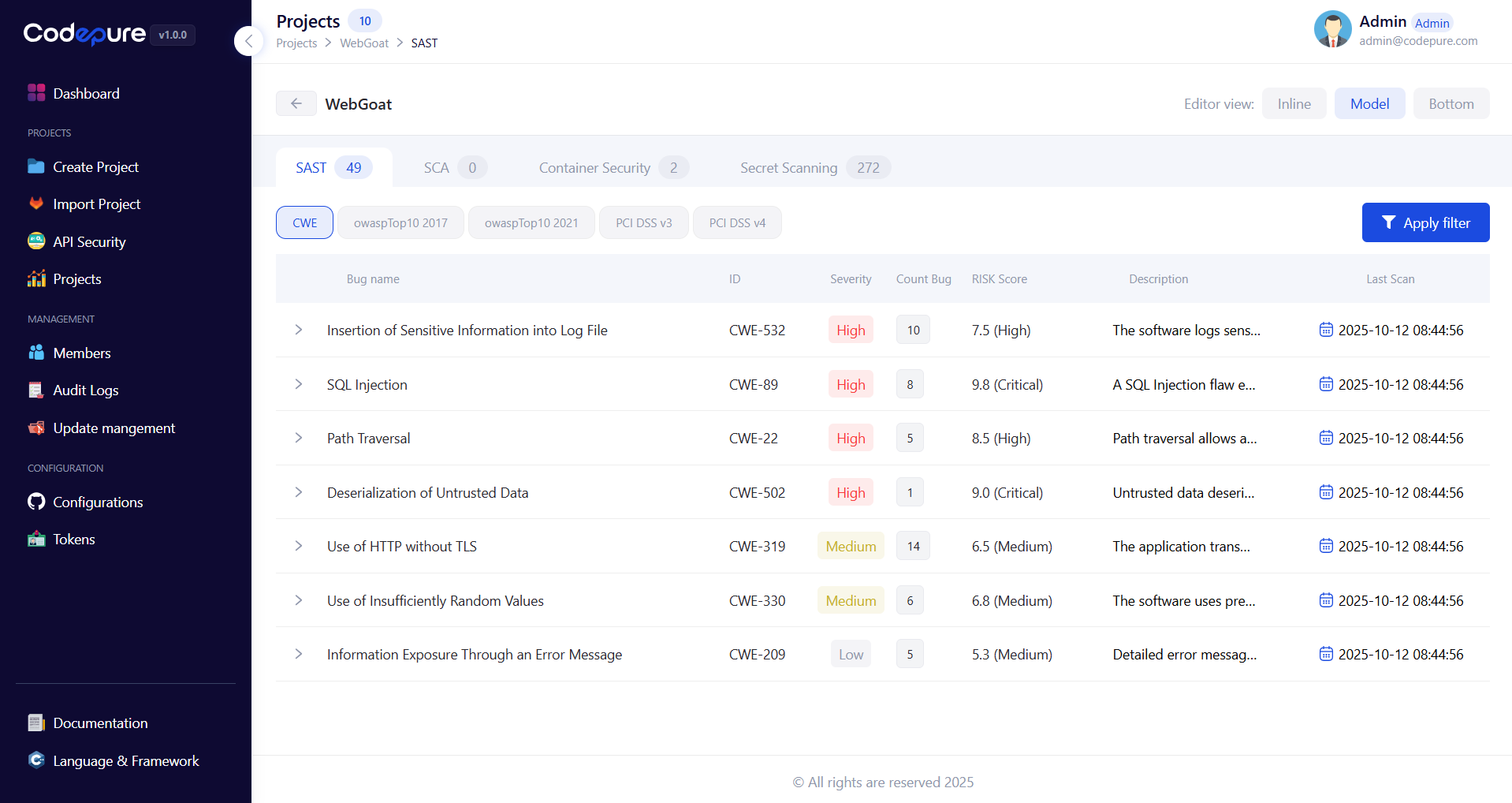
- Severity Levels: Critical, High, Medium, Low, Informational
- Confidence Scores: Likelihood of true positive
- CWE Mapping: Common Weakness Enumeration classification
- OWASP Alignment: Top 10 category mapping
- Compliance Tags: PCI DSS, HIPAA, GDPR relevance
- By severity level
- By vulnerability type (CWE category)
- By compliance standard (OWASP, PCI, ISO)
- By file or component
- By introduction date
- By developer/team
3. Remediate Vulnerabilities
Get actionable fix guidance with code examples: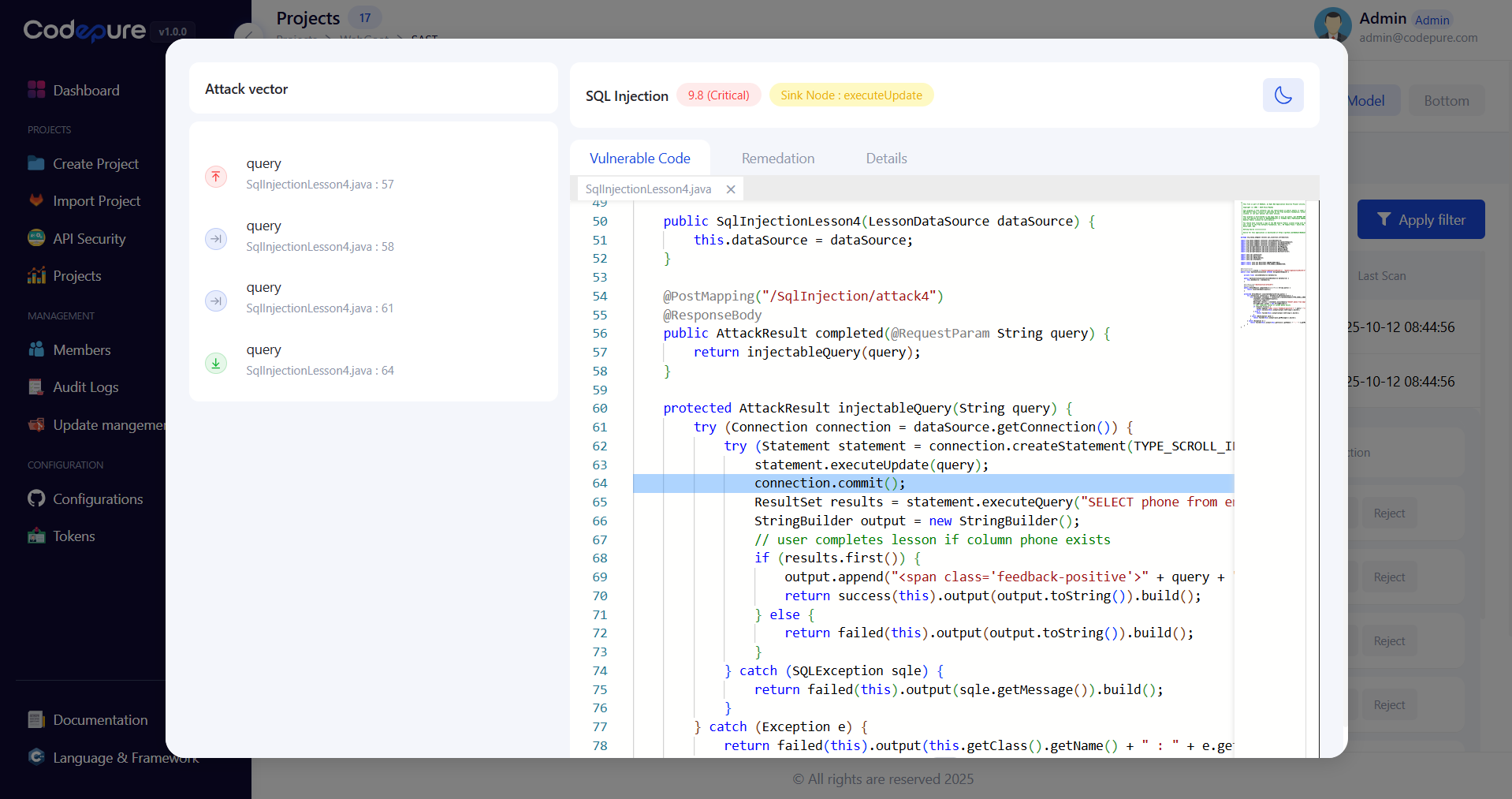
- Detailed Description: Understanding the vulnerability
- Attack Scenario: How the vulnerability could be exploited
- Code Examples: Vulnerable vs. secure code patterns
- Fix Suggestions: Step-by-step remediation guidance
- Auto-Fix: One-click fixes for common issues (where applicable)
- Verification: Re-scan to confirm successful remediation
Advanced Features
Incremental Scanning
Optimize scan times with intelligent incremental analysis:- Scans only modified code and dependencies
- Maintains security context across scans
- Reduces scan time by up to 90%
- Perfect for CI/CD integration

