What is Secret Scanning?
Codepure’s Secret Scanning provides enterprise-grade detection of exposed secrets and sensitive information across your entire development ecosystem. Using advanced pattern recognition, entropy analysis, and machine learning, it identifies credentials before they become security breaches, protecting your organization from unauthorized access and data leaks.Types of Secrets Detected
Cloud Provider Credentials
- AWS: Access keys, secret keys, session tokens, RDS passwords
- Azure: Service principal credentials, storage account keys, CosmosDB keys
- Google Cloud: Service account keys, API keys, OAuth tokens
- IBM Cloud: API keys, resource keys, HMAC credentials
- Oracle Cloud: API signing keys, auth tokens, customer secret keys
- Alibaba Cloud: AccessKey pairs, RAM credentials
Source Control & CI/CD
- GitHub: Personal access tokens, OAuth tokens, App installation tokens
- GitLab: Personal/project access tokens, runner registration tokens
- Bitbucket: App passwords, OAuth tokens, repository access tokens
- Jenkins: API tokens, credentials, secret text
- CircleCI: API tokens, project tokens
- Travis CI: API tokens, encrypted values
Database Credentials
- SQL Databases: Connection strings for MySQL, PostgreSQL, SQL Server, Oracle
- NoSQL: MongoDB URIs, Redis passwords, Cassandra credentials
- Data Warehouses: Snowflake, Redshift, BigQuery credentials
- Message Queues: RabbitMQ, Kafka SASL credentials, SQS/SNS access
API Keys & Tokens
- Payment Gateways: Stripe, PayPal, Square API keys
- Communication: Twilio, SendGrid, Mailgun credentials
- Monitoring: Datadog, New Relic, PagerDuty API keys
- Authentication: JWT secrets, OAuth client secrets, SAML certificates
- Blockchain: Private keys, wallet mnemonics, API credentials
Certificates & Encryption
- SSL/TLS: Private keys, PEM files, PKCS12 certificates
- SSH Keys: Private keys, authorized keys with weak protection
- PGP/GPG: Private keys, signing keys
- Encryption Keys: AES keys, RSA private keys, symmetric keys
Application Secrets
- Environment Variables: .env files, docker-compose secrets
- Configuration Files: application.yml, config.json with embedded secrets
- Package Managers: npm tokens, PyPI passwords, Maven credentials
- Mobile Apps: Firebase keys, Google Services JSON, Apple certificates
- IoT Devices: Device certificates, MQTT credentials, provisioning keys
How Secret Scanning Works
Multi-Layer Detection Engine
1. Pattern-Based Detection
Codepure employs sophisticated regex patterns and rule sets to identify secrets:- High-Entropy String Analysis: Detects random-looking strings likely to be secrets
- Format Validation: Verifies secret patterns match expected formats
- Contextual Analysis: Examines surrounding code for secret indicators
- Custom Pattern Support: Define organization-specific secret patterns
2. Machine Learning Detection
Advanced ML models trained on millions of code samples:- Behavioral Analysis: Identifies secret-like patterns even without exact matches
- False Positive Reduction: ML-based filtering to minimize noise
- Adaptive Learning: Continuously improves based on confirmed findings
- Language-Specific Models: Optimized detection for different programming languages
3. Verification & Validation
Active verification to confirm secret validity:- API Testing: Safely validates if API keys are active (without making changes)
- Format Verification: Confirms secrets match provider specifications
- Entropy Calculation: Measures randomness to identify likely secrets
- Checksum Validation: Verifies secret integrity where applicable
Comprehensive Scanning Coverage
Repository Scanning
- Full History Analysis: Scans entire Git history, including deleted commits
- Branch Protection: Monitors all branches, not just main/master
- Pull Request Scanning: Pre-merge detection to prevent secret introduction
- Submodule Support: Recursive scanning of Git submodules
File System Scanning
- Binary File Analysis: Extracts and scans strings from compiled code
- Archive Inspection: Looks inside ZIP, TAR, JAR files
- Document Scanning: Checks PDFs, Word docs, spreadsheets
- Image Metadata: Scans EXIF data and embedded information
Real-Time Protection
- Pre-Commit Hooks: Prevents secrets from being committed
- IDE Integration: Real-time detection while coding
- CLI Scanning: Command-line tool for local development
- Webhook Monitoring: Instant alerts on secret detection
Why Secret Scanning is Critical
The Growing Threat Landscape
Secret exposure is one of the most common and damaging security vulnerabilities:Industry Statistics
- 83% of organizations have experienced secret leaks in the past year
- Average cost of a secret-related breach: $4.5 million
- 67% of breaches involve compromised credentials
- Exposed secrets are exploited within 7 minutes on average
Common Attack Vectors
- Supply Chain Attacks: Compromised dependencies with embedded secrets
- Insider Threats: Malicious or accidental exposure by employees
- Public Repository Leaks: Secrets accidentally pushed to public repos
- Container Image Exposure: Secrets baked into Docker images
- Log File Disclosure: Credentials logged in error messages
Compliance & Regulatory Requirements
Standards Compliance
- PCI DSS: Requirement 8 - Identify and authenticate access
- HIPAA: Technical safeguards for access control
- GDPR: Article 32 - Security of processing
- SOC 2: Access control and encryption requirements
- ISO 27001: A.9 Access control, A.10 Cryptography
Audit & Reporting
- Automated compliance reports for auditors
- Historical tracking of secret remediation
- Evidence collection for security assessments
- Executive dashboards for security posture
Getting Started with Secret Scanning
Prerequisites
Before initiating secret scanning:- Ensure repository access permissions are configured
- Set up scanning policies and sensitivity levels
- Configure notification channels for alerts
- Establish secret rotation procedures
Step-by-Step Scanning Guide
1. Configure Scanning Scope
Define what to scan and how thoroughly:- Scanning Depth: Choose between quick scan, standard, or deep scan
- File Types: Select specific file extensions or scan all files
- History Range: Scan recent commits or entire repository history
- Exclusions: Define paths or patterns to skip
2. Initiate Secret Scan
From the dashboard:- Select your project or repository
- Choose Secret Scanning from security options
- Configure scan parameters if needed
- Click Start Scanning to begin analysis
- All source code files and configurations
- Commit history and deleted files
- Binary files and archives
- Documentation and comments
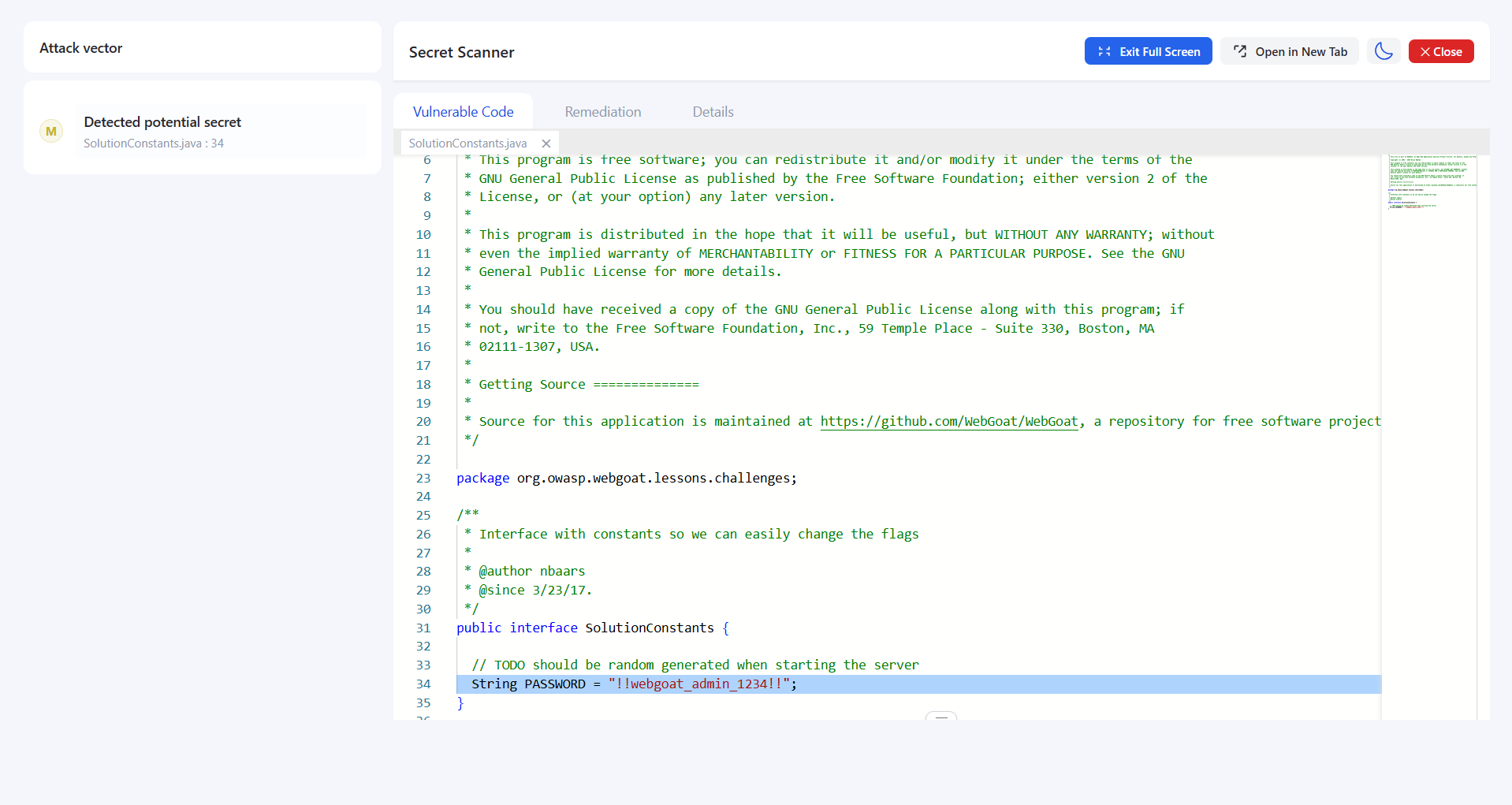
3. Review Detection Results
After scanning completes, access the comprehensive report:- Critical Findings: Active credentials requiring immediate rotation
- High Risk: Valid but potentially inactive secrets
- Medium Risk: Weak or default credentials
- Low Risk: Test credentials or false positives
- Exact file location and line number
- Secret type and potential impact
- Verification status (active/inactive/unknown)
- First and last detection timestamps
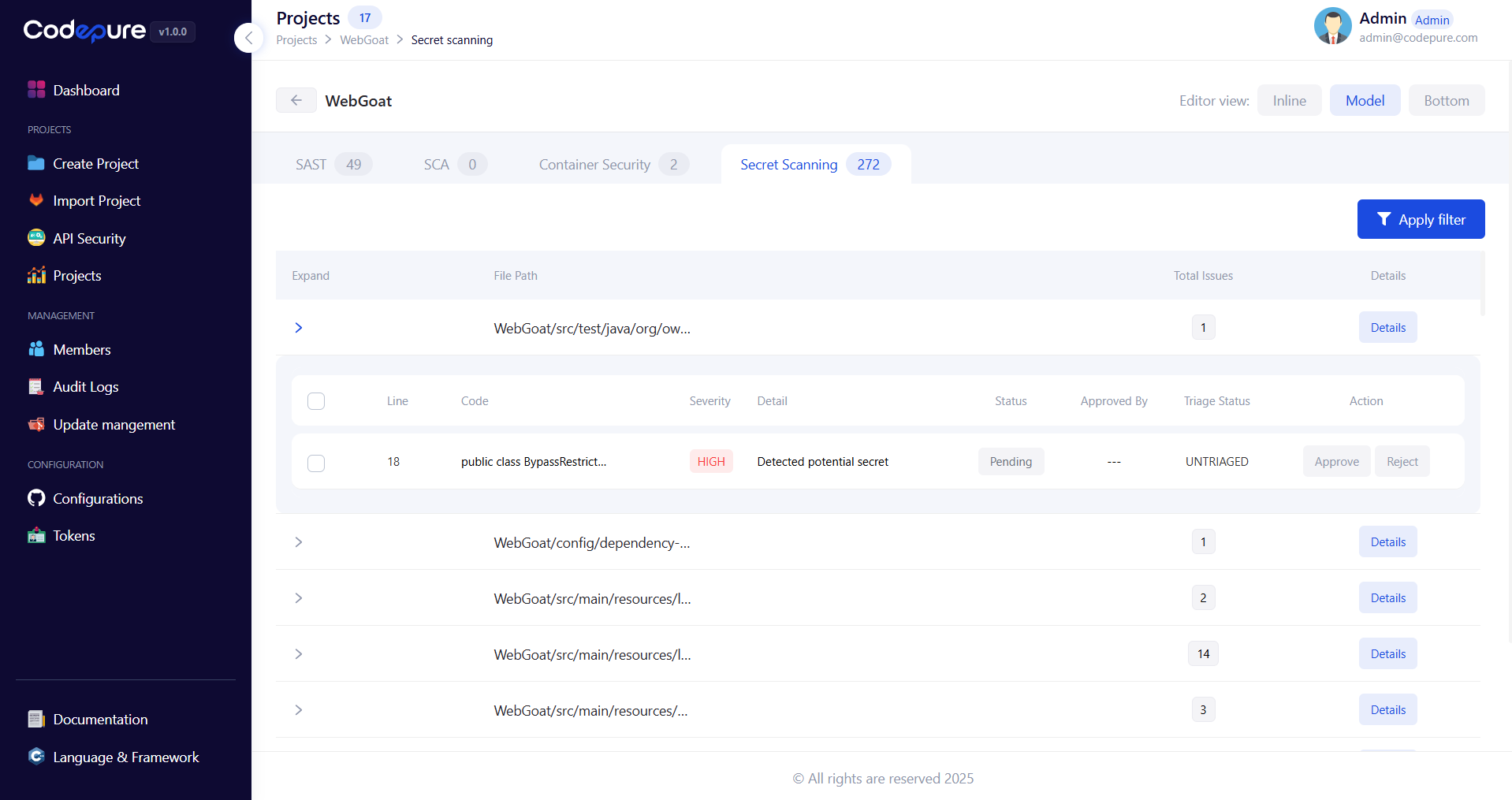
4. Investigate Individual Findings
Click Open on any finding to view:- Secret Details: Type, format, and entropy score
- Code Context: Surrounding code for better understanding
- Exposure Timeline: When the secret was introduced and by whom
- Impact Assessment: Potential systems and services affected
- Similar Findings: Other instances of the same secret
5. Remediate Exposed Secrets
The Remediation section provides step-by-step guidance: Immediate Actions:- Rotate the Secret: Generate new credentials immediately
- Update Applications: Replace old secrets with new ones
- Remove from Code: Delete secrets from source files
- Clean Git History: Remove secrets from commit history
- Implement secret management systems (HashiCorp Vault, AWS Secrets Manager)
- Use environment variables or configuration services
- Enable secret scanning in CI/CD pipelines
- Establish secure coding practices