What is Container Security?
Codepure’s Container Security provides comprehensive scanning and protection for your entire container ecosystem. Whether you’re using Docker, Kubernetes, Docker Compose, or other container orchestration platforms, our security scanner identifies vulnerabilities, misconfigurations, and compliance issues before they reach production.Supported Container Technologies
Docker
- Docker Images: Scans local and registry-hosted images for vulnerabilities
- Dockerfiles: Analyzes build instructions for security best practices
- Docker Registry: Continuous monitoring of images in Docker Hub, Amazon ECR, Azure Container Registry, and private registries
- Multi-stage Builds: Security analysis across all build stages
Docker Compose
- Service Configuration: Validates security settings across all services
- Network Policies: Ensures proper network isolation between containers
- Volume Permissions: Checks for insecure volume mounts and permissions
- Environment Variables: Detects exposed secrets in compose files
Kubernetes
- Pod Security: Scans pod specifications and running containers
- RBAC Policies: Validates role-based access control configurations
- Network Policies: Ensures proper network segmentation
- Secrets Management: Detects hardcoded secrets and improper secret usage
- Helm Charts: Security analysis of Helm chart templates and values
- Admission Controllers: Integration with Kubernetes admission controllers for runtime protection
Additional Platforms
- OpenShift: Full support for Red Hat OpenShift container platform
- Amazon ECS/EKS: Native integration with AWS container services
- Azure AKS: Seamless scanning for Azure Kubernetes Service
- Google GKE: Complete support for Google Kubernetes Engine
- Podman: Security scanning for rootless container environments
How Container Security Works
Comprehensive Scanning Approach
When you initiate a Container Security scan, Codepure performs multi-layered analysis:1. Image Layer Analysis
- Base Image Vulnerabilities: Identifies CVEs in OS and runtime layers
- Dependency Scanning: Analyzes all installed packages, libraries, and frameworks
- Binary Analysis: Detects vulnerabilities in compiled applications
- Distroless Image Support: Specialized scanning for minimal container images
2. Configuration Security
- Dockerfile Best Practices: Validates against CIS Docker Benchmark
- Kubernetes Manifests: Checks against Kubernetes security best practices
- Resource Limits: Ensures proper CPU and memory constraints
- Security Contexts: Validates user permissions, capabilities, and SELinux settings
- Network Exposure: Identifies unnecessary open ports and services
3. Secret Detection
- Embedded Credentials: Finds hardcoded passwords, API keys, and tokens
- Certificate Analysis: Validates SSL/TLS certificates and their expiration
- Environment Variables: Scans for sensitive data in environment configurations
- Configuration Files: Detects secrets in application configuration
4. Compliance Validation
- CIS Benchmarks: Automated checks against CIS Docker and Kubernetes benchmarks
- NIST Guidelines: Compliance with NIST container security guidelines
- PCI DSS: Container-specific PCI compliance requirements
- HIPAA/SOC2: Healthcare and service organization compliance checks
- Custom Policies: Define organization-specific security policies
Scanning Modes
Pre-Build Scanning
Analyze Dockerfiles and configuration files before building images to catch issues early in the development cycle.Build-Time Scanning
Integrate with CI/CD pipelines to scan images automatically during the build process.Registry Scanning
Continuous monitoring of container registries to detect newly discovered vulnerabilities in stored images.Runtime Protection
Real-time monitoring of running containers in Kubernetes clusters for active threat detection.Why Container Security is Critical
Container adoption continues to grow, but with it comes unique security challenges:Key Benefits
Shift-Left Security
- Identify vulnerabilities during development, not in production
- Reduce remediation costs by catching issues early
- Integrate security into DevOps workflows seamlessly
Supply Chain Protection
- Verify the integrity of base images and dependencies
- Track the provenance of container components
- Ensure only approved images are deployed
Compliance Assurance
- Automated compliance reporting for audits
- Continuous monitoring for policy violations
- Evidence collection for regulatory requirements
Risk Reduction
- Prevent container breakouts and privilege escalation
- Eliminate hardcoded secrets and credentials
- Ensure proper network segmentation and isolation
Getting Started with Container Security
Prerequisites
Before running container security scans, ensure you have:- Container images available locally or in a registry
- Proper authentication credentials for private registries
- Network access to Codepure scanning infrastructure
Step-by-Step Scanning Guide
1. Configure Your Environment
First, set up your scanning environment by selecting the appropriate configuration:- Docker Standalone: For individual Docker hosts
- Docker Compose Project: For multi-container applications
- Kubernetes Cluster: For orchestrated container deployments
- Container Registry: For centralized image scanning
2. Select Scan Target and Initiate Scan
Choose your scanning target:- Local Images: Scan images on your Docker host
- Registry Images: Scan images from Docker Hub, ECR, ACR, or private registries
- Running Containers: Scan active containers in your environment
- Kubernetes Workloads: Scan deployments, pods, and services
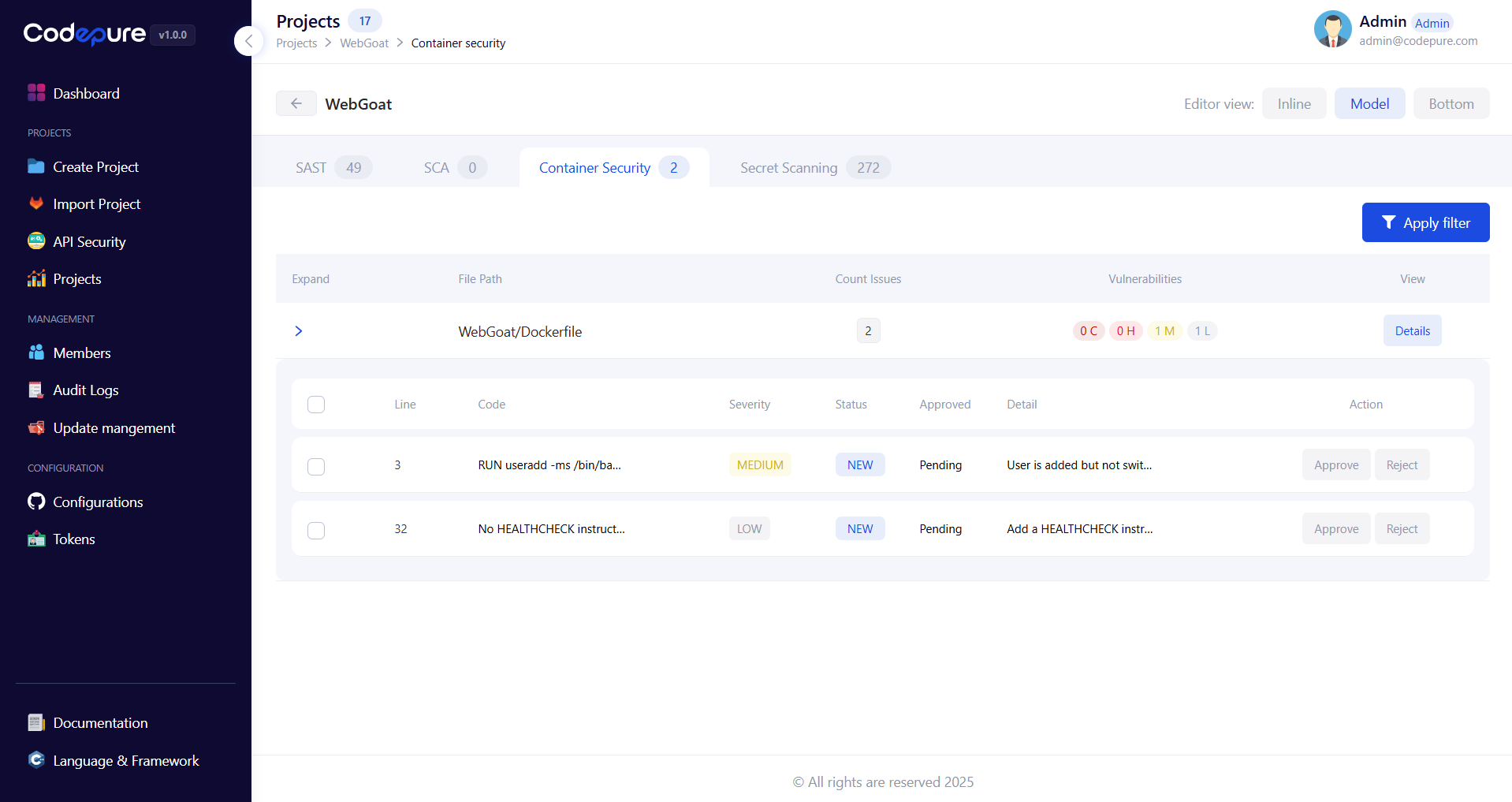
3. Review Scan Results
After the scan completes, you’ll see a comprehensive security report:- Critical Vulnerabilities: High-priority issues requiring immediate attention
- Configuration Issues: Misconfigurations and policy violations
- Compliance Status: Pass/fail status for various compliance frameworks
- Secret Exposures: Detected credentials and sensitive data
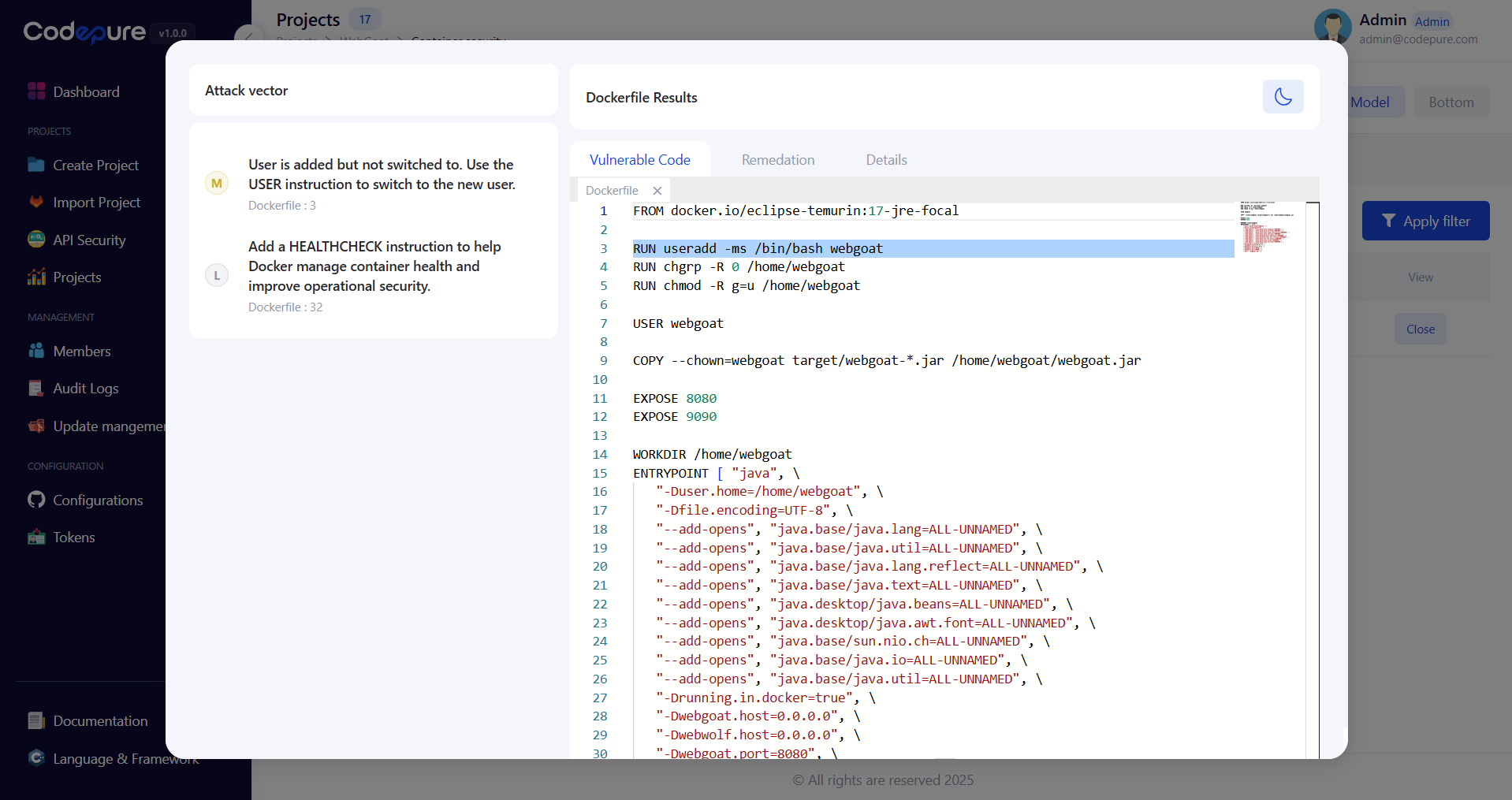
4. Analyze Individual Findings
For each detected issue, Codepure provides:- Severity Rating: Critical, High, Medium, or Low
- CVSS Score: Industry-standard vulnerability scoring
- Affected Components: Specific packages or configurations
- Attack Vector: How the vulnerability could be exploited
- Business Impact: Potential consequences if exploited
5. Implement Remediation
Click Open on any issue to access detailed remediation guidance:- Quick Fixes: Immediate actions to resolve the issue
- Best Practices: Long-term improvements for security posture
- Alternative Solutions: Different approaches based on your constraints
- Validation Steps: How to verify the fix is effective
- Updating base images to patched versions
- Removing unnecessary privileges and capabilities
- Implementing proper secret management
- Applying security policies and network controls